Use Shakudo Keycloak with an External OIDC Provider
Introduction to OpenID Connect (OIDC)
OpenID Connect (OIDC) is an identity layer on top of the OAuth 2.0 protocol. It enables clients to verify the identity of an end-user based on the authentication performed by an Authorization Server, as well as to obtain basic profile information about the end-user in an interoperable and REST-like manner. This guide will assist you in configuring Shakudo Keycloak to use an external OIDC Identity Provider (IDP).
This guide will allow you to log into Shakudo using external IDPs such as Microsoft or Google through Shakudo Keycloak.
Information Table
| Information | Example Value | Source | How to Obtain |
|---|---|---|---|
| Redirect URL | https://your-app.com/callback | Your Application | Provided by your application. Typically found in the application's OAuth settings. |
| Client ID | external-idp-client-id | External IDP | Provided by your external identity provider when you register the application/client. |
| Secret ID | xyz123secureVeryLongSecret | External IDP | Provided by your external identity provider in the client's security credentials. |
| OIDC Discovery Endpoint | https://idp.example.com/.well-known/openid-configuration | External IDP | Check your external identity provider's documentation or admin console. |
Prerequisites for External OIDC Provider Setup in Shakudo Keycloak
Shakudo Keycloak Server Installation
- Ensure that you have a running instance of Shakudo Keycloak server.
- You can visit the Shakudo Keycloak admin console with
<Domain>/auth/
Administrative Access
- Access to the Shakudo Keycloak Admin Console with administrative privileges to manage external identity providers.
- Ensure that you have the necessary credentials for accessing your external IDP.
Knowledge of OIDC Protocol
- Familiarity with OpenID Connect (OIDC) protocol and its concepts like tokens, scopes, and claims.
Configuring Shakudo Keycloak with an External OIDC Provider
To configure Shakudo Keycloak to use an external OpenID Connect (OIDC) Identity Provider, follow these steps:
Log in to Shakudo Keycloak Admin Console
- Open your Shakudo Keycloak Admin Console in your web browser.
- Enter your administrator credentials to log in.
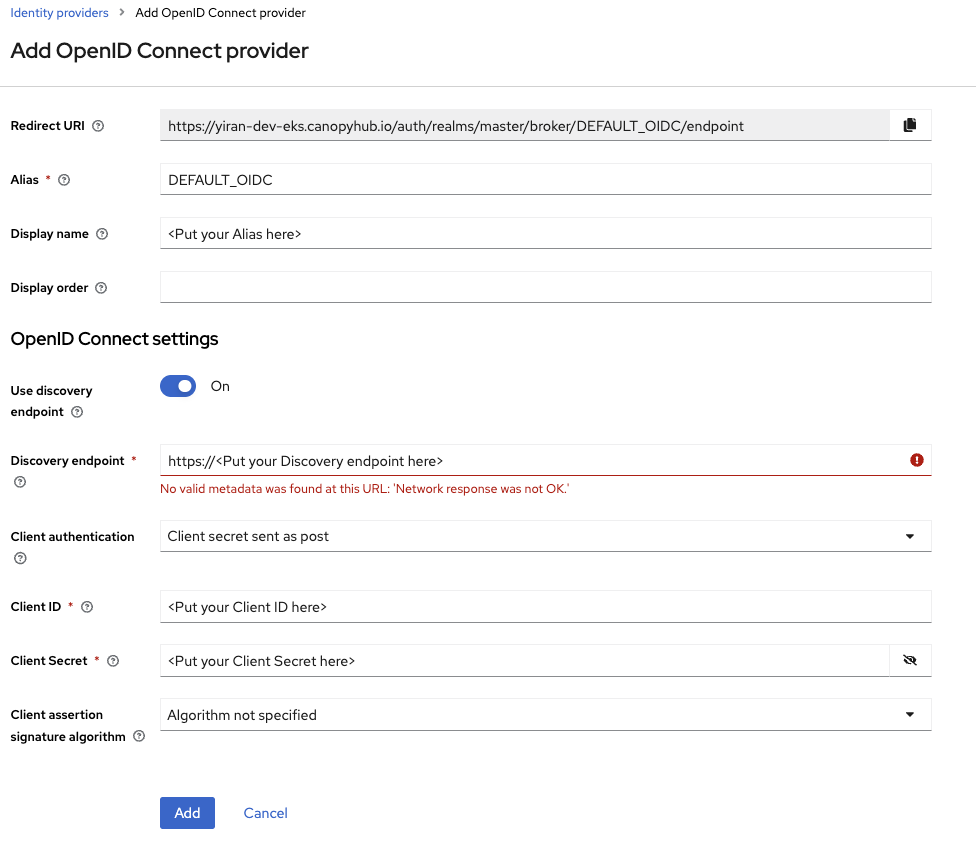
Add an External Identity Provider
- Go to the "Identity Providers" section in your realm settings.
- Click on "Create" and choose "OpenID Connect v1.0" from the list of available providers.
Enter the External IDP Details
- Alias: Provide a unique alias for your identity provider.
- Client ID: Enter the client ID obtained from your external IDP.
- Client Secret: Provide the client secret associated with your application on the external IDP.
- Discovery URL: Enter the OIDC discovery URL for your external identity provider.
- Save the configuration.
Advanced Settings (Optional)
- Configure scopes and claims mapping if needed, based on the specific requirements of your external IDP.
- Adjust token settings and user attribute synchronization as required.
For more information on how to set up IDP mappers in Shakudo Keycloak, please refer to the IDP Mapper Setup.